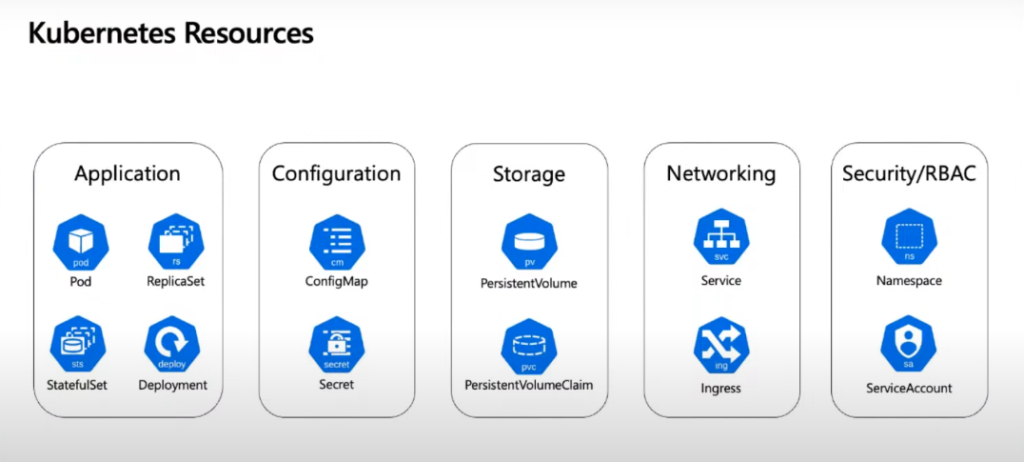
Kubernetes has become the de facto standard for container orchestration, providing a robust framework for managing containerized applications. To fully harness the power of Kubernetes, it’s crucial to follow best practices in several key areas: Application Management, Configuration, Storage, Networking, and Security/RBAC. This blog post explores best practices in each of these areas to help you optimize your Kubernetes deployments.
1. Application Management
1.1. Use Declarative Configurations
- Best Practice: Define your application deployments, services, and other resources using YAML manifests. This ensures that configurations are versioned and can be tracked in version control systems.
- Why: Declarative configurations make it easier to manage changes, rollbacks, and audit configurations.
1.2. Implement Rolling Updates
- Best Practice: Use rolling updates for deploying changes to minimize downtime and ensure a smooth transition between versions.
- Why: Rolling updates help maintain application availability and provide a fallback in case of issues.
1.3. Leverage Health Checks
- Best Practice: Configure liveness and readiness probes for your pods to ensure that Kubernetes can detect and respond to application failures.
- Why: Health checks help maintain application reliability and prompt automatic recovery from failures.
1.4. Use Resource Requests and Limits
- Best Practice: Set CPU and memory requests and limits for your containers to manage resource allocation effectively.
- Why: This prevents resource contention and ensures that your application gets the resources it needs without affecting other workloads.
2. Configuration Management
2.1. Centralize Configuration with ConfigMaps and Secrets
- Best Practice: Store configuration data and sensitive information in ConfigMaps and Secrets, respectively.
- Why: Centralizing configuration makes it easier to manage and update application settings without changing code.
2.2. Use Environment-Specific Configurations
- Best Practice: Maintain separate configurations for different environments (development, staging, production) and use tools like Helm or Kustomize to manage these configurations.
- Why: This approach helps in maintaining consistency and isolating environment-specific settings.
2.3. Version Control Your Configurations
- Best Practice: Store all Kubernetes manifests and configuration files in a version control system (e.g., Git).
- Why: Version control provides history, collaboration, and rollback capabilities for configuration changes.
3. Storage Management
3.1. Use Persistent Volumes (PVs) and Persistent Volume Claims (PVCs)
- Best Practice: Manage stateful applications by using Persistent Volumes and Persistent Volume Claims to decouple storage from pods.
- Why: This ensures that data persists even if pods are rescheduled or restarted.
3.2. Implement Storage Classes
- Best Practice: Define and use Storage Classes to manage different types of storage (e.g., SSDs, HDDs) and configure dynamic provisioning.
- Why: Storage Classes allow you to tailor storage solutions to your application’s needs and automate provisioning.
3.3. Regularly Backup and Restore
- Best Practice: Implement a regular backup strategy for your persistent data and test restore processes.
- Why: Regular backups protect against data loss and ensure business continuity.
4. Networking
4.1. Use Network Policies
- Best Practice: Define Network Policies to control the traffic between pods and services within your cluster.
- Why: Network Policies enhance security by restricting communication based on rules.
4.2. Implement Service Discovery
- Best Practice: Utilize Kubernetes services and DNS for service discovery to enable pods to communicate with each other.
- Why: Service discovery simplifies the management of dynamic network endpoints in a distributed environment.
4.3. Optimize Ingress Controllers
- Best Practice: Configure Ingress Controllers to manage external access to your services and optimize load balancing and routing.
- Why: Proper Ingress configuration enhances application availability and security.
5. Security and RBAC
5.1. Implement Role-Based Access Control (RBAC)
- Best Practice: Use RBAC to define roles and permissions for users and service accounts, restricting access to resources based on need.
- Why: RBAC enforces the principle of least privilege, reducing the risk of unauthorized access.
5.2. Secure API Access
- Best Practice: Secure access to the Kubernetes API server using authentication mechanisms (e.g., certificates, tokens) and enforce HTTPS.
- Why: Securing API access prevents unauthorized interactions with your cluster.
5.3. Regularly Update and Patch
- Best Practice: Keep your Kubernetes cluster, nodes, and containers up to date with the latest security patches and updates.
- Why: Regular updates help protect against vulnerabilities and ensure compatibility with new features.
5.4. Monitor and Audit Security Events
- Best Practice: Implement monitoring and auditing tools to track security events and anomalies in your Kubernetes environment.
- Why: Monitoring and auditing provide visibility into potential security issues and help with compliance.
Conclusion
Managing Kubernetes resources effectively requires attention to detail across several critical areas. By following best practices in application management, configuration, storage, networking, and security/RBAC, you can ensure a well-optimized, secure, and reliable Kubernetes environment.
Adopting these practices not only enhances the stability and performance of your Kubernetes deployments but also prepares you to handle the complexities of modern containerized applications. Embrace these best practices to make the most out of Kubernetes and drive your cloud-native applications towards success.


